Written in collaboration with Carla Santos, a member of The Blog team.
As financial services continue to evolve, the need for innovative solutions has become paramount rather than a luxury. Yet, in their race to deliver cutting-edge digital services, financial institutions face a familiar tension: how to remain agile and customer-centric while maintaining the robust governance, risk management, and compliance (GRC) controls required by regulators and stakeholders alike.
Luxembourg Private Bank (LPB)*, a forward-looking private banking institution, offers a compelling case study in how to navigate this challenge. With an IT strategy anchored in innovation, cyber and operational resilience, safe AI integration, and the deep embedding of GRC within its IT architecture, the bank has struck a rare balance. This integrated approach has not only enhanced agility and customer service but also fortified trust and compliance in a complex regulatory environment.
*Disclaimer: LPB is a fictional organisation. The scenarios and insights presented are based on input from various IT leaders in mature financial institutions.
Recent research supports this strategic alignment. According to the PwC Global Risk Survey 2023, organisations with a defined technology strategy—one that includes investment in technology to drive resilience and/or manage risks—are more likely to:
- express strong confidence in their ability to balance growth with effective risk management;
- view Generative AI (GenAI) more as an opportunity than a risk;
- report improved financial performance because of effective risk mitigation.
In this context, LPB’s approach isn’t just sound—it’s strategic.
In this blog, we sit down with LPB’s Chief Information Officer (CIO) to explore how the bank has harmonised its IT strategy and GRC initiatives. The interview unpacks the thinking behind this approach, how integration between GRC and IT architecture was achieved, and the tangible business outcomes that followed. Fictional as LPB may be (and its CIO), the lessons drawn from its story are anything but. Financial institutions seeking a blueprint for resilient digital transformation can take inspiration from it—and find a practical path forward.
Integrating GRC into IT Architecture
Let’s start with the big picture. What does your current IT architecture landscape look like, briefly?
In a few words, we have a muti-layered architecture (front-end, business logic, data, and integration), primarily using cloud infrastructure with minimal on-premises systems. The cloud services drive scalability and flexibility, while on-premises infrastructure is reserved for specific legacy systems or regulatory requirements.
We have integrated Continuous Integration/Continuous Delivery (CI/CD)1 pipelines across the layers to enable constant delivery, seamless updates, and fast iteration. We also use Commercial-off-the-shelf (COTS)2 solutions for standardised, non-differentiating functions like procurement, human resources and marketing, optimising cost and efficiency.
However, for differentiated capabilities or specialised needs, such as advanced analytics or custom integrations, we develop tailored solutions, ensuring they align with business strategy and offer a competitive edge.
Many financial institutions struggle with GRC being perceived as separate from core IT strategy. How has LPB approached this integration?
Our philosophy centres on making GRC an inherent characteristic of our technology landscape rather than an external constraint. We’ve achieved this through the multi-layered architectural approach. At the infrastructure level, we’ve engineered compliance checks directly into our cloud infrastructure, eliminating the traditional segregation between infrastructure teams and compliance officers.
In our development environments, we’ve moved beyond periodic audits by implementing policy-as-code3 across most of our CI/CD pipelines. This approach ensures every code commit is automatically assessed against both functional requirements and compliance standards. Perhaps most significantly, we’ve transformed our operations by integrating real-time risk monitoring with our IT service management platform, creating a unified view of system health and compliance status.
The results speak for themselves: tasks that once required weeks of audit preparation are now performed continuously, saving over 40% of the time while also enhancing our release velocity.
For legacy applications or COTS solutions that aren’t natively using CI/CD, we have adopted a two-pronged strategy:
- First, we integrate these applications into the broader CI/CD framework by using Application Programming Interfaces (APIs) to enable more automated deployments and policy compliance checks;
- Second, the bank is progressively refactoring or replacing legacy systems with cloud-native, CI/CD-compatible solutions. This transition helps further streamline operations, reduce reliance on manual audits, and maintain a high standard of compliance and operational oversight, while gradually modernising its technology stack.”
Market insights:
ServiceNow’s internal GRC transformation is a strong example of an integrated approach. By using its own platform to automate and integrate workflows, it reduced quarterly control certification efforts by 66%, cut control testing time by 50%, and saved US$2.6m annually.
Enabling innovation through compliance
There’s a persistent industry narrative that positions GRC as an innovation inhibitor. How does your experience challenge this assumption?
We’ve fundamentally reframed this relationship by designing compliance into our innovation processes from inception. When we develop new digital products, GRC requirements are treated as first-class citizens alongside functional specifications.
Our mobile banking platform development is a compelling example. By establishing pre-approved technology stacks with built-in controls and creating automated exception management workflows, we reduced what traditionally would have been a 14-week approval process down to almost half the time to ensure compliance with both internal processes and relevant regulations such as the General Data Protection Regulation (GDPR), the revised Payment Services Directive (PSD2) and the Digital Operational Resilience Act (DORA), among others.
This isn’t about cutting corners; it’s about engineering compliance into the development lifecycle. We’ve found that when developers have clear guardrails and automated compliance checks built into their toolchains, they actually become more innovative, not less. They spend less time worrying about retrospective fixes and more time creating value.
For COTS solutions, we conduct various internal assessments to ensure they align with both functional and regulatory requirements before being integrated into our IT landscape. This strategy not only ensures that COTS solutions meet compliance and operational standards but also enables the bank to innovate quickly and efficiently while maintaining a high level of control and governance.
Market insights:
The PwC Global Compliance Survey 2025 shows that adopting a compliance-by-design approach is one of the most effective ways to stay ahead of regulatory change and the disruptions reshaping today’s markets.
Ensuring cybersecurity and operational resilience
In an era of escalating cyber threats and geopolitical tensions, how does your GRC-IT integration enhance security posture?
Our approach transforms cybersecurity from a periodic assessment to a continuous characteristic of operations. We implement always-on control monitoring across all IT assets to create a living compliance posture rather than a point-in-time snapshot. We map all systems to the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF)4, which provides our security team and regulators with relevant visibility:
- For the security team, mapping enables continuous tracking of system status, allowing for the quick detection of gaps, vulnerabilities, or non-compliance in security controls, and supporting a proactive response to emerging threats.
- For regulators, it offers a transparent, auditable record of the bank’s cybersecurity practices, reinforcing accountability and regulatory alignment.
Perhaps most impactful has been the use of the AI-driven threat modelling within our integrated GRC tool, which inherently accounts for evolving cybersecurity threats and vulnerabilities. This means when we evaluate potential vulnerabilities or design new controls, we’re simultaneously addressing security and compliance objectives.
The operational impact has been significant: we have sharply reduced the average time to remediate critical vulnerabilities, while also strengthening our cybersecurity regulatory compliance and maturity.
Market insights:
According to the PwC 2024 Global Digital Trust Insights, GenAI can be invaluable for proactively detecting vulnerability exploits, rapidly assessing their extent and presenting tried-and-true options for defence and remediation. GenAI can identify patterns, anomalies and indicators of compromise that often elude traditional detection systems, enhancing both the speed and accuracy of threat detection.
AI strategy: making AI safe and effective
Many banks struggle with AI projects because of ‘model risk’—essentially, the possibility that an AI system could make wrong decisions, behave unfairly, or break rules without anyone noticing. How does LPB avoid these pitfalls while still innovating?
We bake safety and fairness into our AI systems from day one. Think of it like seatbelts and airbags being built into a car rather than added later. When our data scientists implement new AI tools, they follow our internal AI governance guidelines as well as use special software that automatically checks for problems. Examples of such tools in the market include TensorFlow Model Analysis, AI Fairness 360, DataRobot or SonarQube.
With this approach, we basically try to tackle the following questions: is the AI making fair decisions? Can we explain how it works? Does it follow all banking rules? These checks happen at every step, long before the AI ever interacts with customers.
For example, our virtual assistant that helps customers with banking questions went through hundreds of these automatic tests before launch. The system constantly monitors itself too. If it starts behaving differently over time, it alerts our team immediately. This helped us significantly reduce AI mistakes compared to older systems.
The best part? Because we’ve proven we can manage these risks well, our AI teams can move faster. New features that used to take months to approve now get the green light in weeks, as long as they pass all our built-in safety checks.
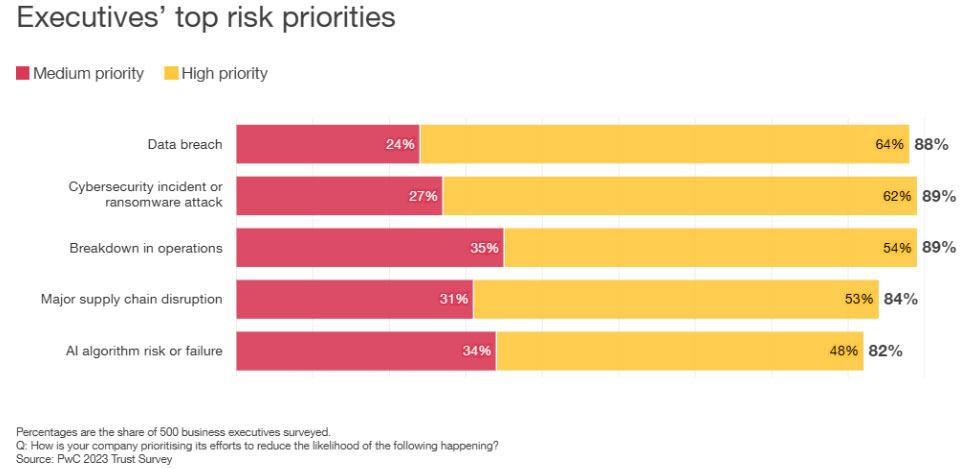
Market insights:
We have outlined a seven-step approach to managing AI risks, based on insights from the 2023 Trust Survey. The approach entails:
-
- Setting risk-based priorities;
- Revamping cybersecurity, data and privacy protections;
- Addressing opacity risk;
- Equipping stakeholders for responsible use and oversight;
- Monitoring third parties;
- Keeping a close eye on the evolving regulatory landscape;
- Implementing automated oversight mechanisms.
The path forward: reframing GRC as a strategic advantage
Looking ahead, what lessons would you share with peers who are beginning similar transformation journeys?
One of the most important lessons has been recognising that GRC and IT strategy are not only compatible, but also mutually reinforcing when properly integrated. The institutions that will thrive in the coming years are those that stop viewing GRC as an obstacle and start treating it as a strategic capability.
The ultimate measure of success isn’t just fewer audit findings or faster release cycles. It’s measured by the ability to deliver innovative financial products that customers trust implicitly because they know our systems are secure and compliant by design. That’s the competitive edge of a truly integrated GRC-IT approach.
However, a mindset shift may be needed: from viewing GRC as a box-ticking exercise to viewing it as a foundation for secure innovation. CIOs who harness risk management, regulation, and compliance as strategic elements within their IT strategy can drive real business impact.
This approach can yield a range of benefits, including enhanced security and resilience, as well as business improvements through innovation and automation, all within a controlled and secure environment. Crucially, securing strong support from top management is essential to ensuring the success of such initiatives.
We hope LPB’s story has helped demonstrate how a resilient digital transformation is possible by integrating GRC principles into your IT strategy. But sometimes, theory only goes so far. If you are looking for concrete steps or tailored guidance, visit our webpage or reach out to our team of specialists.
What we think

The value of GRC becomes evident when it’s embedded in the DNA of IT strategy—guiding decisions, aligning with business goals, leveraging technology to drive innovation and efficiency, and creating a foundation that fuels trust within and outside the organisation.
Integrating GRC into IT strategy allows organisations to proactively manage risks and maintain regulatory compliance while fostering innovation. Although balancing flexibility with control and continuous monitoring presents challenges, effective implementation enhances security and drives a competitive edge.

Notes:
- CI/CD is a set of practices that automate the process of integrating code changes and delivering software updates quickly and reliably.
- COTS refers to ready-made software or hardware products that are commercially available for general use, rather than custom-built.
- Policy-as-code is the practice of defining and automating policies through code to ensure consistent and enforceable governance in software systems.
- The NIST Cybersecurity Framework (CSF) provides a set of guidelines and best practices for organisations to manage and reduce cybersecurity risks.